If you own a popular website or blog, you would have definitely heard about Cryptojacking. It has been one of the most serious threats that emerged, affecting even the commonest people around. There are actually two sides to this problem of Cryptojacking, depending on how this thing is implemented. It’s kind of okay if you, the website owner, inserted the Crypto-Mining script into your website so that you can earn bit of revenue without using ads. At the same time, it’s a huge violation of your privacy policy and the respect you have for your visitors. That having said, things are obviously different if you didn’t insert the code.

Well, as strange as it might sound, some hackers might have got into your website and inserted the Crypto-Mining code into it. I mean, just think of it: hackers find it an awesome way to have constant revenue, which increases according to the number of visitors your website has. Now, this is not really good for your privacy, health of your website or the overall reputation. It also means that you no longer have complete control on your website. In other words, it is the right time to remove the Cryptojacking script from the website and to take some preventive steps.
We do understand that some of you might not understand the concept of Cryptojacking. So, it makes sense to start with an introduction to Cryptojacking and Coinhive and then move onto the possible solutions.
Cryptojacking and Coinhive – an Introduction
In the simplest terms, Cryptojacking happens when an attacker hijacks a user’s browser and uses their CPU resources for mining cryptocurrencies. Since the process of Bitcoin mining is impractical, the resources are used to mine lightweight ones like Monero. Anyway, chances are, the computers of the infected users would become incredibly slow, especially in some cases. If you are the one who put up the Cryptojacking code, you will receive the mined Monero coins, but that’s not the case.
You should also know about Coinhive before proceeding further. Coinhive was the first solution for utilizing visitors’ CPU resources for cryptocurrency mining. As you can guess, the method was launched as an effective alternative to annoying advertising. The point was that you can keep earning without bothering the visitors — at the same time, draining their CPU performances and battery lives in the long run. Anyway, owners of websites were required to insert the Coinhive script into the code and all the users would be affected.
So far, we have talked about how you can insert the Coinhive code into your website voluntarily. Things are not going to sound right if someone else did that, right? In that case, you won’t be the one receiving the total revenue either.
How to Find If Your Website Is Affected by Crypto-Mining Script?
Before we proceed further, it is important to confirm whether your website is really affected. The process is very simple:
You have to visit your website from different computers equipped with anti-malware protection. A powerful antivirus program will be able to detect the Coinhive script that is working in background. Upon the detection of the script, you can confirm the presence of the malicious Crypto-Mining code. We recommend repeating the process from different devices — say Windows and Mac, for instance. Once you have an idea, stop the search and let’s talk about the crypto-mining script removal.
Now, here is the better part of confirmation. In most cases, Coinhive insertion is done through source code of the website. It may happen in different ways. For instance, if you had installed a nulled script from a not-so-trusted sources, the script could have included Coinhive elements as well. So, another way to completely confirm the presence of Cryptojacking script is to check out the source code of your website. You can do that from your common web browser.
Open the source code and see if the word ‘Coinhive’ is presented in the main code section. If it’s in, let’s go.
How to Remove Coinhive Miner from Your Website?
This is not tough as it may sound. Let’s talk about the commonest way of infection first. There is less chance that your entire website is owned by a hacker. In that case, you would have seen some other symptoms as well. However, we would surely recommend taking a few precautionary steps like ensuring the safety, using stronger passwords and enhancement of overall security. Once you have done that, and confirmed that the website is under your control, we can start the search for the crypto-mining script.
Now, this step requires some technical knowledge since you are going to deal with code. Depending on the CMS you are using, you can open the main file of your website and search the code for a possible line that deals with Coinhive. In common cases, the code may look like the following:
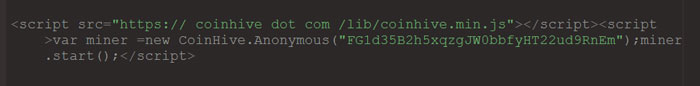
If the same script is present in your website, don’t think much and remove it. For the removal process, you may need some expert help. This is the idea: crypto-mining scripts normally affect the main page of website. So, it’s recommended that you hand over the process to someone with experience. Once the removal has been done, it means you are completely safe and that your users won’t suffer from CPU draining when they visit your website.
As an extra precaution method, you should clear the server cache as well, especially if you are using CDN in your website. This will remove the possibility that Coinhive scripts may work from the cache.
P.S. The threats of crypto-mining scripts are not reducing day by day. On the other hand, you can see newer ones coming up every day. For instance, there was the presence of another Cryptojacking script named Minr that is so hard to be detected. So, we recommend taking a look at this side every once in a while.
Some Steps to Stay Safe
We already mentioned the different ways how your website may get infected by Cryptojacking script. You’d not mind the results of the following methods if you would like to keep the situation away.
- Make sure that you are not using any pirated scripts, themes or other codes that may consist of the cryptocurrency script.
- Follow all the security procedure for keeping your website away from hackers and other attacks that can offer them control.
- Always update the CMS and Server Software to the latest version. If the script made its way to your website via some vulnerabilities, this step will stop that.
Hope you have an idea about how to keep your websites safe from Cryptojacking scripts.
The Wrap-Up Part
Just as we said earlier, the process of removing the Coinhive crypto-mining script if your website is affected is simple than you thought. You might need some familiarity with code, but you can always get some help from a friend. If you have a popular blog, we recommend that you have a dedicated team for security and technical aspects. Anyway, we hope this guide helps you to not only remove the existing Coinhive Cryptojacking infection but also for preventing future scripts from infecting your site.
Meta: Are you suspicious that your website is affected? Here is a guide that helps you remove Coinhive crypto-mining script from an infected website.